1. Introduction
Two-way relaying
is an effective method for addressing key challenges in wireless networks, including reliability, spectral efficiency, and energy constraints [
1,
2,
3]. In
two source nodes exchange data through one common relay(s), which processes the received data and forwards the processed data to both sources. In [
4,
5,
6], the common relays perform an XOR operation on the packets received from the two sources and then broadcast the XOR-ed packet back to them. Therefore, this scheme is known as the three-phase Digital Network Coding
. Moreover, the schemes introduced in [
4,
6] operate in cognitive radio
environments, where the transmit power of the secondary users is limited by an interference threshold set by the primary users. In [
7,
8,
9], the authors proposed two-phase Analogue Network Coding
schemes, where the common relays amplify the signals received from two sources during the first phase and then broadcast the amplified signals to both sources in the second phase. Although the
schemes achieve higher throughput than the DNC TWR ones, the sources in
must perform interference cancellation, which is too complex to implement in practice. In [
10,
11,
12,
13], joint Successive Interference Cancellation
and
are applied at the common relays and these
schemes also use only two phases for the data exchange. In particular, during the first phase, both sources simultaneously transmit their packets to the common relays with different transmit power levels. The common relays then perform
to decode the received packets. Finally, the relays apply
to the decoded packets and transmit the
packet to both sources in the second phase. Recently, many
models utilizing new communication techniques have been developed, proposed, and analyzed. The authors in [
14,
15] studied the performance of the
schemes using radio-frequency energy harvesting
, where the transmitters have to harvest energy from the radio signals of the surrounding nodes to transmit data. In [
16,
17,
18], the TWR schemes using full-duplex
techniques were proposed, where the source and/or relay nodes were equipped with multi-antennas. Although the
schemes use only one time slot for the data exchange between two sources, they require high synchronization between all nodes as well as complex interference cancellation implementation. However, the related works in [
4,
5,
6,
7,
8,
9,
10,
11,
12,
13,
14,
15,
16,
17,
18] did not consider fountain coding
, which is studied in this paper.
Fountain coding
[
19,
20] can be efficiently used in wireless communication applications due to its simple implementation and environment condition adaptation ability. In fact, an
source encodes its data to generate encoded packets (or
packets), which are continuously sent to a destination. The destination only needs to collect a sufficient number of
packets to recover the original data from the source. Another advantage of
is to provide high information security. As proven in [
21,
22,
23], if the destination receives a sufficient number of
packets before the eavesdroppers, the source data will be secure. The authors in [
24] proposed a cooperative transmission model that employs
, non-orthogonal multiple access
, cooperative jamming technique, and intelligent reflective surfaces
(or reconfigurable intelligent surface
) to enhance secrecy performance.
or
are flat-structured surfaces whose arrays of passive and programmable components used to reflect incoming signals to the intended receivers for enhancing the quality of the received signals [
25,
26]. Published works [
27] evaluated secrecy performance of
-assisted wireless communication networks with presence of an eavesdropper. The authors in [
28] proposed a down-link system where a multi-antenna base station uses
to serve two users with the help of
. Additionally, both continuous and discrete phase shifting were considered in [
28]. Another report [
29] also considered the
-assisted wireless communication system using
, and evaluated the performance of the proposed system in an interference-limited environment. In [
30], the authors considered a multi-IRS down-link scheme utilizing wirelessly
. Recently, the
schemes using
have gained much attention of researchers. In [
31], the authors evaluated outage probability
and average throughput of
-aided
schemes, where two sources communicate through the
(instead of common relays in the conventional
schemes). Reference [
32] analyzed performance of
-aided
networks employing
, in terms of
and ergodic rate. The authors in [
33] proposed three power allocation algorithms for
-based Decode-and-forward
models to improve the system sum rate. In [
34,
35],
-aided TWR networks using full-duplex techniques were proposed and analyzed. However, the published works [
27,
28,
29,
30,
31,
32,
33,
34,
35] did not apply
into the
-based
systems.
This paper investigates schemes that incorporate , , and wirelessly energy harvesting . In our model, two secondary sources aim to exchange data with the help of a RIS deployed in the network. Using , one source continuously sends packets until the other source has collected enough to fully recover the original data. Moreover, the transmit power of each source is adjusted based on an interference constraint set by a primary user and the energy harvested from a power station. The new points and main contributions of this work are summarized as follows:
- –
Firstly, this paper considers two schemes, i.e., conventional scheme (named Cov-Scm) and modified scheme (named Mod-Scm). The purpose of proposing the Mod-Scm scheme is to enhance the reliability of data transmission and reduce delay time, compared to the Cov-Scm.
- –
Secondly, we derive closed-form expressions for at each source, system outage probability , and average number of packet transmissions needed for successful data exchange in the proposed schemes over Rayleigh fading channels.
- –
Next, simulation results are presented to validate our analytical findings and compare the performance of the considered schemes.
- –
Finally, we examine the effects of key parameters on overall performance. The results also present that the Mod-Scm scheme obtains better performance, as compared with the Cov-Scm scheme, in terms of reliability (OP, SOP) and delay time (average number of FC packet transmission).
The remaining structure of this paper is as follows:
Section 2 describes the system model for the considered
schemes along with operational principles. In
Section 3, we compute the performance via mathematical expressions.
Section 4 validates the analytical findings through simulations. Finally,
Section 5 gives important conclusions and insights.
2. System Model
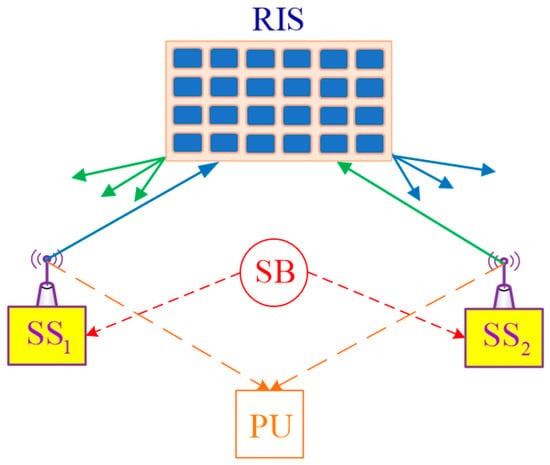
Figure 1 shows the system model of the proposed
-based
model, where secondary sources (
and
) exchange data with each other.
Let and denote the data sent by and , respectively. Since direct communication between and is outage due to their far distance, a reconfigurable intelligent surface is deployed to assist these data exchange. Let represent the number of small reflective elements in the . Additionally, a power beacon station (denoted by ) is deployed in the secondary network to provide energy for and . To prevent co-channel interference, the frequencies used for energy harvesting differ from those used for the data transmission. The transmit power of and is constrained by an interference threshold established by a primary user (). Assume that all channels experience block Rayleigh fading and that all devices are single-antenna nodes.
The proposed scheme can be applied to IoT networks, where and are IoT devices with limited power and energy. Therefore, the station power (SB) is deployed to provide energy for two source nodes. Moreover, due to spectrum scarcity, the underlay cognitive radio technique is employed for the IoT networks.
Following the operational principle of divides into small, equally sized packets, which are then used to create packets. Let denote one FC packet of . To successfully recover , must collect at least packets . In addition, let as the maximum number of packets sent by For simplicity in presentation and analysis, we can assume that and .
In the conventional scheme , continuously transmits packets to through the . After transmission times, stops the transmission. If correctly receives at least packets , the data transmission is successful, and otherwise, experiences an outage. Then, in turn transmits packets to through the , also using transmission times. Similarly, for the successful recovery of , must receive at least packets by the end of this transmission.
In the modified scheme , first transmits packets to . If gathers enough packets after transmission times , sends an ACK message back to . Upon receiving the ACK message, ends its transmission, and begins its transmission. Notably, if , does not need to send feedback to because must stop its transmission, regardless of whether has received enough packets or not. Otherwise, if , the remaining transmission times can be allocated to in the second transmission phase, i.e., allowing to send at most packets to . Similarly, as soon as receives enough packets , it also sends an ACK message to inform .
Remark 1.In the scheme [36], the data transmission of and operates independently, making the transmission order of and irrelevant. However, in the scheme, the system performance depends on whether or transmits first (this issue will be examined in Section 4). Moreover, the scheme always uses a total of transmission times, while the scheme uses fewer, because the transmission stops as soon as each source gathers enough desired packets. Let
represent the channel gains between nodes X and Y, and its distribution functions expressed as
where and are cumulative distribution function and probability density function of , respectively, [36] with being the path-loss factor and being the physical distance between and .
Let
as the distance between the node
and the
reflector component of the
, where
,
. As assumed in [
37], we can assume that all the distances
are identical, i.e.,
(
)
.
Considering the transmission of a packet
from
to
via the
. Assume that the total delay for each transmission of
is normalized to 01 (time unit). During the interval
,
harvests energy from
, and its harvested energy can be calculated as
where represents a conversion efficiency, and is the transmit power of .
The remaining interval
is allocated for the transmission of
. Therefore, the average transmit power of
can be formulated as
where Moreover, the transmit power of must satisfy the interference threshold set by PU, i.e.,
where is the interference threshold.
From Equations (3) and (4), the transmit power of
can be formulated by
Next,
transmits
to
, and the received signal at
is given as (see [
38,
39,
40]):
where and are channel coefficients of the and links, respectively, is response of the component of the , is the modulated signals of , and is zero-mean Gaussian noise at . We assume that variance of all Gaussian noises is identical and equal to , i.e., .
We note that
and
, where
and
are amplitude of
and
, respectively. Moreover, we can express
and
in exponential form as follows:
and
, where
and
are phases of
and
, respectively. Similarly to [
37], we can express
as
, where
is the phase response of
, which can be optimally adjusted by
. Therefore, the maximum
obtained at
for decoding
can be given as
where .
Using [
37], we can obtain
of
as
where and are gamma and lower incomplete gamma functions [41], respectively, and
From Equations (7) and (8), we can see that
and
have the same
. Hence, we can omit the subscripts
and
, i.e.,
Then, we can obtain
of
and
as
Differentiating Equation (9) with respect to
, we obtain
of
and
as
Next, setting
, we see that
is also a random variable whose
can be formulated as
Substituting Equation (1) into Equation (12), we obtain
where .
Finally, the channel capacity of the
link can be formulated as
4. Simulation and Analytical Results
Section 4 validates the formulas derived in
Section 3 using Monte Carlo simulations. Throughout this section, we fix positions of two sources and the
node at
,
,
, and
, while the
station is positioned at
, where
. We also assign values to the following parameters as follows:
,
, and
(see
Table 1). In all results, we fix
, and denote the simulation and analytical results by
and
, respectively. It is noted that our derived expressions are applicable to all parameter values in practice. The reason we fix the values of these parameters is to focus on analyzing the impact of the key parameters (i.e.,
) on the OP and SOP performance of the considered schemes. Next, as shown in figures below, the
and
results align closely, verifying the accuracy of our derivations.
Figure 2 illustrates the probability of the unsuccessful transmission of the packet
as a function of
in dB with
and
. As seen, both
and
decrease as
increases. This is due to the fact that increasing
also increases the transmit power of
and
. Additionally,
and
with
are lower than those with
, which is due to the improved quality of the
links at higher values of
. We also observe from
Figure 2 that
is lower than
. This is because
is closer to
than
, resulting in a higher average transmit power for
as compared to
.
Figure 3 presents
as a function of the fraction of time
allocated for the
operation. The system parameters in this figure are set to
and
. We can see that both
and
change significantly with variations in
. It is straightforward that with very low values of
, the transmit power of
is also low, resulting in the low channel capacity and high
. However, when
is very high, the time allocated for the data transmission phase is reduced, which also leads to low channel capacity and high
. Therefore,
reaches its lowest value at a medium value of
. For example, with
,
and
obtain their minimum values at
. In addition, the position of
significantly impacts on
and
. Indeed, as shown in
Figure 3, the value of
as
is lowest (highest) because
is nearest (farthest) to
. When
,
is lower than
because
is closer to
than
.
In
Figure 4, we present
at two sources in the
scheme as a function of
(dB) when
,
and
. With
, the distance from
to
is shorter than that from
to
, resulting in
, and
at
is lower than that at
. Hence, we observe from
Figure 4 that the
performance of
is better than that of
for all values of
and
. It is also shown that
of both sources decreases when the values of
and
increase. Furthermore, the
gap between the two sources also increases as
increases. It is worth noting that the results obtained in this figure can be used to design/optimize the OP performance. For example, with
, the OP of both sources in the Cov-Scm is lower than 0.01 when the value of
is from 11 dB to 20 dB. In other words, the SB station can use a minimum transmit power of 11 dB to ensure that OP of both sources remains below 0.01.
Figure 5 shows
at two sources in the
scheme as a function of
(dB) when
,
, and
. Furthermore, we consider two scenarios: (i)
transmits first (named
); (ii)
transmits first (named
). We observe that in
,
of
is lower than that of
at low and medium
values, and at high
values,
of
is higher. In
,
of
is always better than that of
for all values of
. Moreover, the
gap between the two sources in
is much higher than that in
, and
at
and
in
are lowest and highest, respectively. Therefore,
Figure 5 shows that
achieves greater performance fairness for two sources.
To determine whether
or
performs better,
Figure 6 compares
of all the considered schemes. In this figure, the parameters are set to
,
, and
. As shown,
obtains the best
performance, while that of
is worst. We also observe that
of
is much lower than those of
and
. Therefore, in this simulation, the source
in
should be prioritized to transmit its data first.
Figure 7 presents both
and
of the considered schemes as a function of
when
8.5 dB,
, and
. It is noted that because SB is located at
, we have
; hence, in
,
of
is lower than that of
. As emphasized in
Section 3, we can confirm from
Figure 4 that
of
in
is equal to that of
in
, and
of
in
is equal to that of
in
. This figure also shows that there are optimal values of
at which
of each user is lowest. For example, in
, the
performance at
and
is best when
and
, respectively. For the
performance, we see that
obtains the best performance, while
still outperforms
. Similarly, there exists optimal values of
which provides the best
performance for the considered schemes. Based on the results obtained from
Figure 6 and
Figure 7, we can conclude that in the
scheme, if
(then
of
is lower than that of
), hence, the source
should be prioritized to transmit data first. Now, let us consider examples of designing the proposed schemes. If the required quality of service (QoS) dictates that the SOP performance must be below 0.01, then, as shown in
Figure 7, only the
scheme can satisfy this requirement. Moreover, the value of
must be designed within the range of 0.325 to 0.4. For another example, to determine the optimal value of
in the
scheme, we follow the following steps:
- –
Step 1: As shown in
Figure 7, the simulation and theoretical results of the SOP performance over a wide range of
were used to confirm the existence of an optimal value of
.
- –
Step 2: Identifying the interval that contains the optimal value of
. For example, in
Figure 7, the interval of
is (0.325, 0.4).
- –
Step 3: Using the derived expression of SOP (i.e., Equation (27)) to search the optimal value of within the interval determined in Step 2.
Figure 8 studies the impact of the positions of the power station
on the
and
performance when
11 dB,
,
, and
. Due to the symmetry, we can see that in
,
of
at
equals to that of
at
where
. Similarly,
of
in
at
equals to that of
in
at
. For the
performance, we see that
of
is symmetrical about
, while
of
at
equals to that of
at
. Therefore, as
, the source
should be selected to transmit data first. Finally, it is worth noting from
Figure 8 that the
of
,
, and
is lowest when
,
, and
respectively.
In
Figure 9, we present the average number of transmissions of
packets for the successful data exchange between two sources in the
scheme as a function of
(dB) when
,
, and
. It is worth noting that the number of transmissions in
is always
.
Figure 9 presents that the average number of transmissions in
and
decreases with the increasing of
When the
values are high enough, the average number of transmissions in
and
will reach
. Therefore, the proposed
scheme not only obtains a better
and
performance, but also achieves a lower average number of transmissions. As shown in
Figure 9, the average number of transmissions of
is lower than that of
. However, at high
regimes, the performance of
and
is almost the same. Finally, as observed, increasing the number of reflective elements in the
also reduces the average number of transmissions significantly.
Figure 10 presents the impact of
on the average number of transmissions of
packets for the successful data exchange between two sources in the
scheme when
dB,
, and
. As seen in
Figure 10, the average number of transmissions in
and
achieves the minimum value as
. Moreover, the positions of the
station also impacts the average number of transmissions significantly. In this figure, the average number of transmissions in
and
with
is the same, and is lowest as compared with
and
.